How To?:
Clean the Initialized DATA section within ME/TXE Regions
Management Engine 11 - 15 & TXE 3 - 4
In this section we have taken as an example a SPI/BIOS image dump of a model which comes with CSME firmware version 11.0.x.xxxx and SKU Consumer H. However, the same applies to all CSME 11 - 15 and CSTXE 3 - 4 firmware.
1. From Intel (Converged Security) Management Engine: Drivers, Firmware and Tools 558 or Intel (Converged Security) Trusted Execution Engine: Drivers, Firmware and Tools 223 threads, make sure you have downloaded the correct System Tools package and extract it.
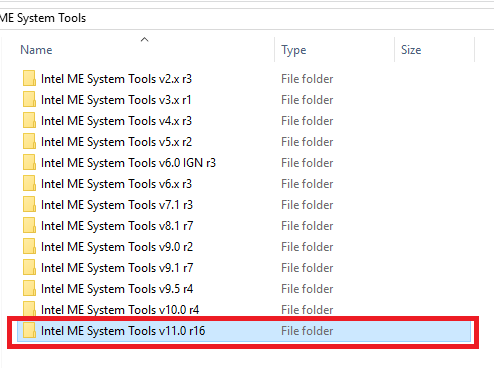
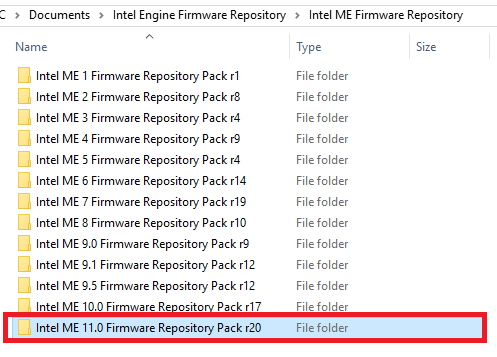
2. From Intel (CS)ME, (CS)TXE, (CS)SPS, GSC, PMC, PCHC, PHY & OROM Firmware Repositories 389 thread, make sure you have downloaded the correct Repository pack based on major/minor version and extract it.
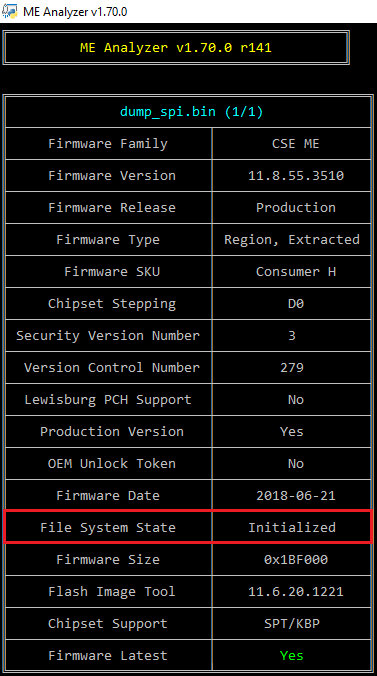
3. Open the dumped SPI/BIOS image with ME Analyzer to see what major/minor version we need as well as SKU. In this case we have:
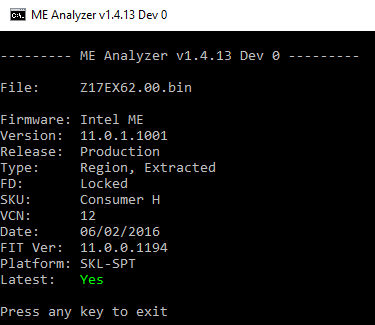
So our SPI/BIOS image dump has a CSME 11.0 firmware with Consumer SKU.
4. Browse the Repository pack, copy the same (or as similar as possible) CSME/CSTXE RGN firmware of the same SKU and major/minor version (as instructed above) somewhere and then rename it to "ME Region.bin" for CSME 11, "TXE Region.bin" for CSTXE 3, "ME Sub Partition.bin" for CSME 12 or "TXE Sub Partition.bin" for CSTXE 4, depending on what you're working with. In this case:
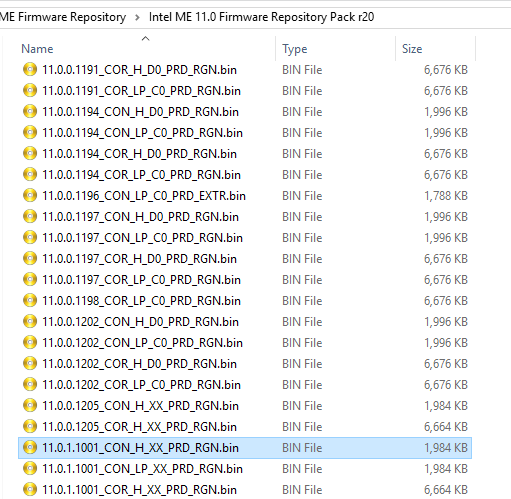
So we pick the firmware file 11.0.1.1001_CON_H_XX_PRD_RGN which matches perfectly what we saw at ME Analyzer. If for example the dumped SPI/BIOS image had CSME 11.0.0.1196 with LP SKU, we would have picked CSME 11.0.0.1197 instead because the one we wanted is EXTR and not RGN. Thus, we rename the "11.0.1.1001_CON_H_XX_PRD_RGN.bin" copy to "ME Region.bin".
5. Open the dumped SPI/BIOS image with ME Analyzer. In order to verify that the SPI/BIOS dump has Initialization data, make sure that File System State is reported as "Initialized".
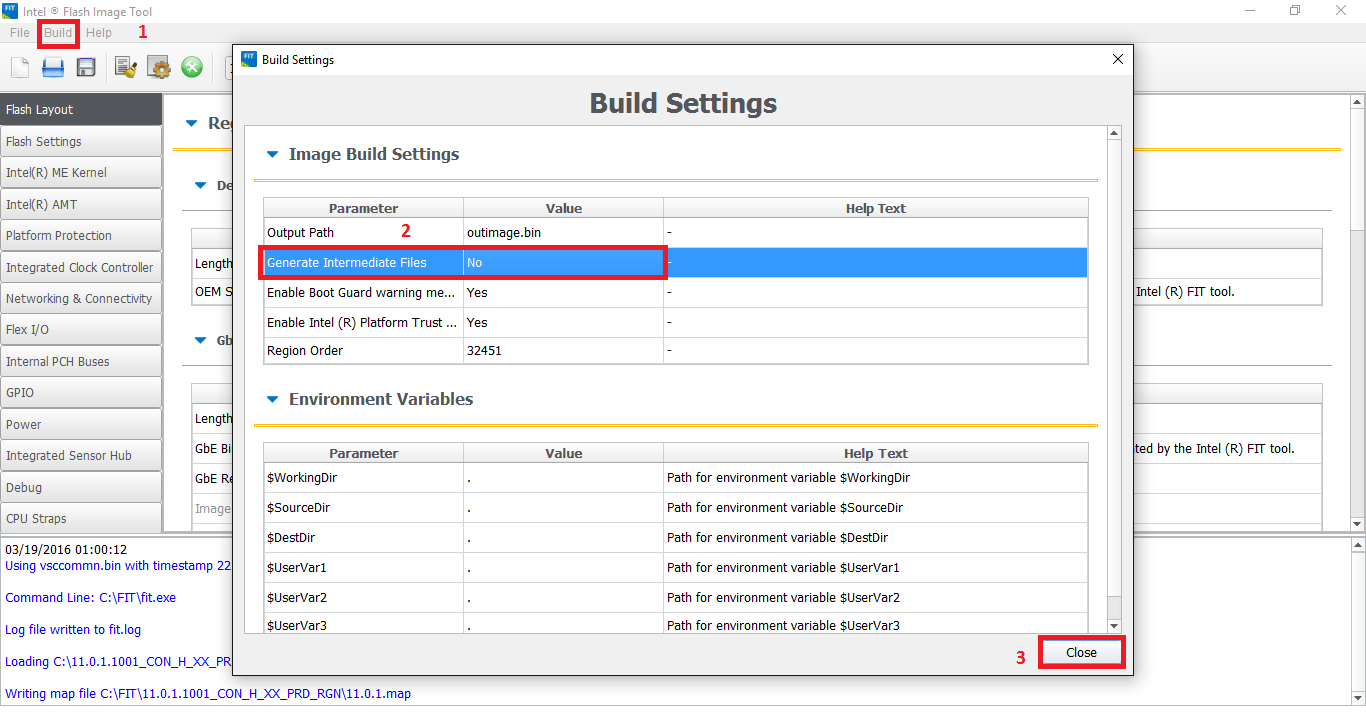
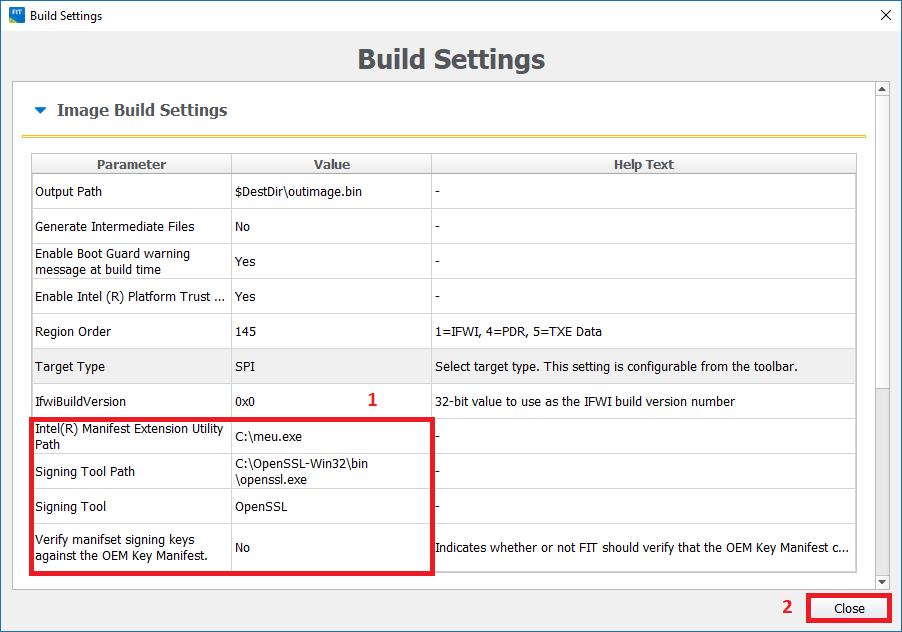
6. From the System Tools folder, go to Flash Image Tool > WIN subfolder and run fit.exe. Drag & drop the dumped SPI/BIOS image you want to clean. Go to "Build > Build Settings", select "No" at the option to "Generate Intermediate Files", leave all other settings intact and click Close.
Note: If you are working on a CSME 11 Engine region only (extracted via Flash Programming Tool with "-me" parameter or via UEFITool > ME region > Extract as is...) and not a full SPI/BIOS image (Flash Descriptor + Engine + BIOS), you also need to change three additional settings. Set "Flash Settings > Flash Components > Number of Flash Components" to 0 and remove the path from both "Flash Layout > Intel(R) ME Region > Intel (R) Trace Hub Binary" and "Integrated Sensor Hub > ISH Data > PDT Binary File" only if these are not present at your dumped CSME 11 Engine region (indicated by the zero-byte size of these modules at the "Decomp" subfolder).
7. If you are working on a CSTXE 3 - 4 SPI/BIOS image, go to "Platform Protection > Platform Integrity" section.
- Check if "OEM Public Key Hash" field exists and whether it is empty/zeroed or not. If "OEM Public Key Hash" field is either missing or empty/zeroed, proceed to the next step of the guide.
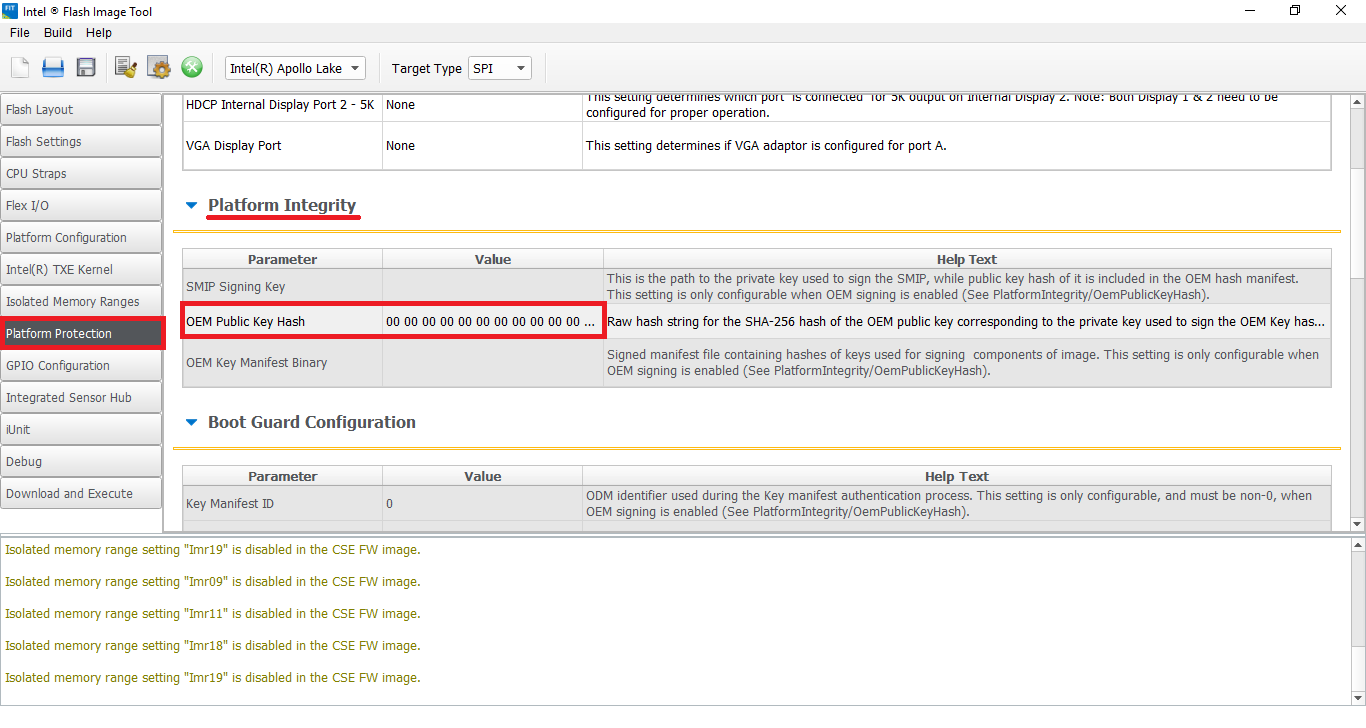
- If "OEM Public Key Hash" is populated then it is highly probable that your SPI/BIOS image is signed by the OEM and their OEM Public Key Hash is stored permanently in the Chipset hardware. In such case, you cannot easily/quickly clean the Engine firmware because the platform will reject it without the OEM's RSA Private Key.
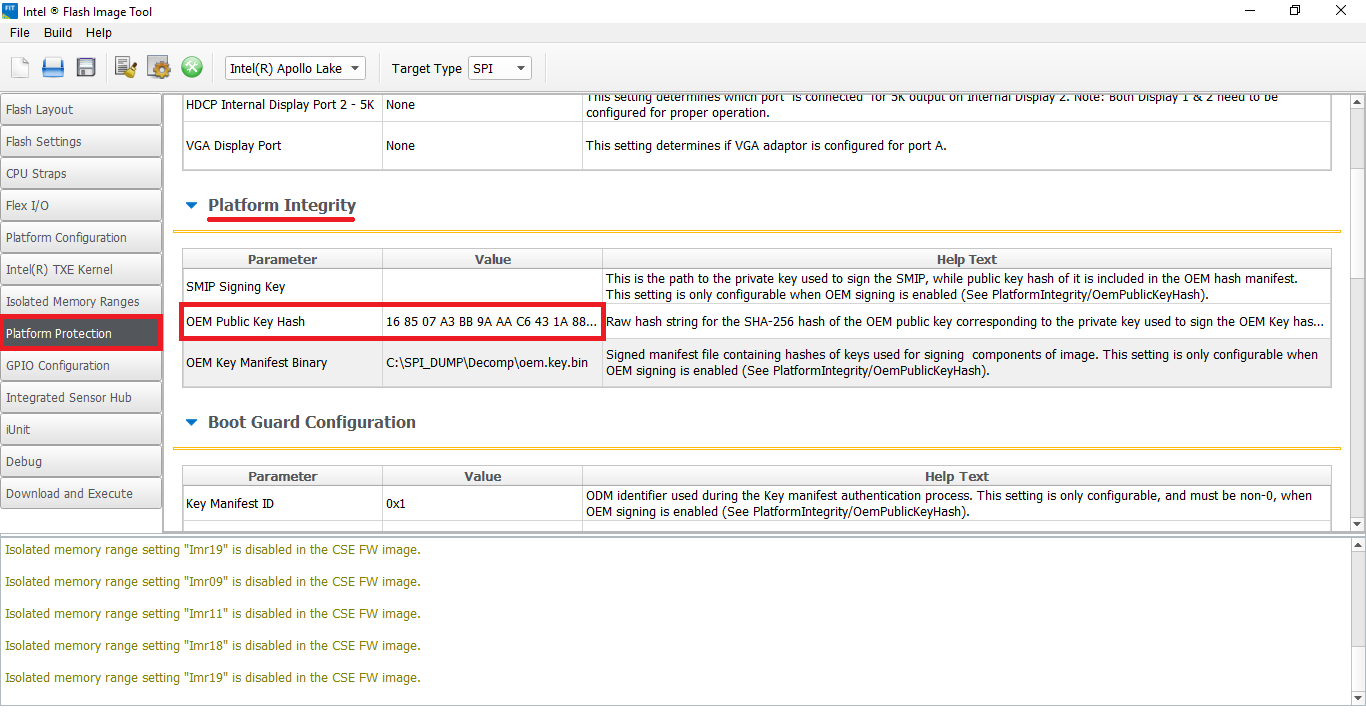
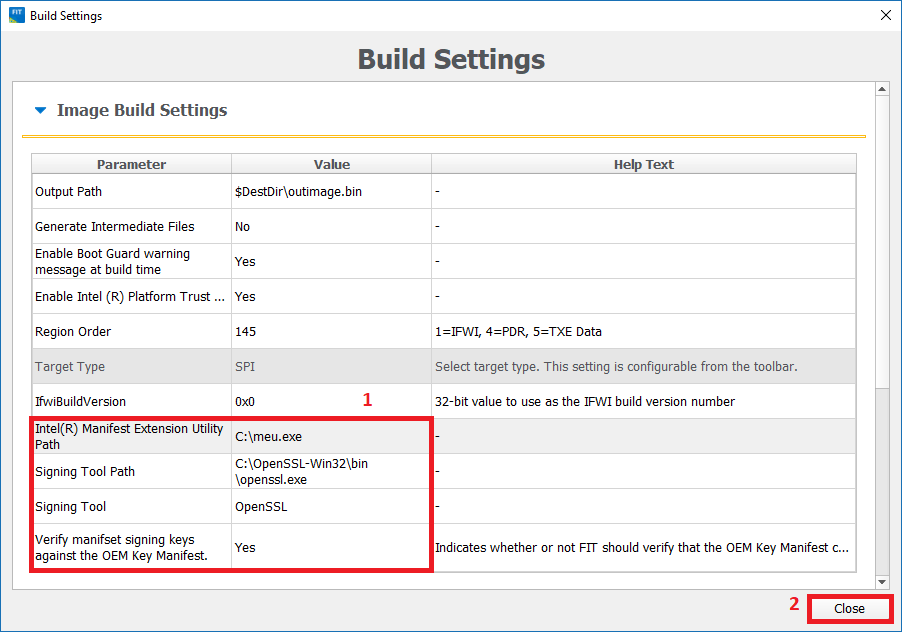
- If you happen to have the OEM's Private RSA Key (unlikely unless you're the OEM), you can input it at "SMIP Signing Key" field. Then go to "Build > Build Settings", input the Manifest Extension Utility (MEU) executable location at "Intel(R) Manifest Extension Utility Path" field, input Win32 OpenSSL Lite 542 executable location at "Signing Tool Path" field, make sure that "OpenSSL" is selected at "Signing Tool" field, make sure that "Verify manifest signing keys against the OEM Key Manifest" is set to "Yes", leave all other settings intact and click Close. Now proceed to the next step of the guide.
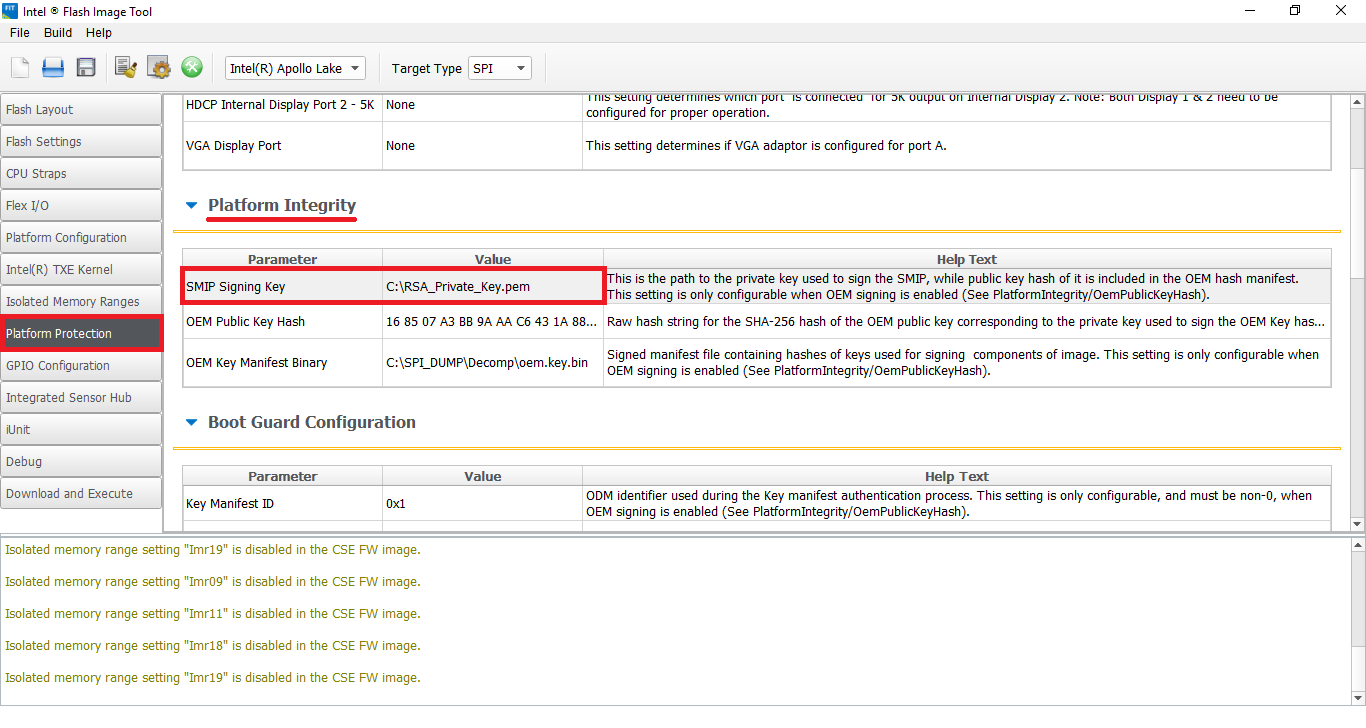
- If you don't have the OEM's Private RSA Key (expected end-user situation), you can still clean the Engine firmware section(s) of the SPI/BIOS image but more steps are needed. That's because the Engine firmware is signed independently and thus protected on its own so any FIT-configurable RSA Public Key Hashes & Signatures relate only to the rest of the BIOS/IAFW/IFWI components of the SPI/BIOS chip image. For example, the "SMIP Signing Key" found above "OEM Public Key Hash" field is used to sign/re-sign the SMIP BIOS/IAFW module which may interact with the Engine firmware but it's not actually a part of it. Thus, the goal is to update the Engine firmware only, without touching the BIOS/IAFW modules, like SMIP or DnX, which require re-signing upon rebuilding the SPI/BIOS image at FIT.
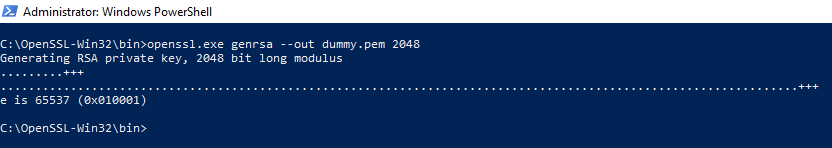
- We need to create a dummy/placeholder RSA Private Key to insert at "SMIP Signing Key" field. The use of OpenSSL is required for that. Under Windows, install Win32 OpenSSL Lite 542, go to its directory and execute the command:1
openssl.exe genrsa --out dummy.pem 2048
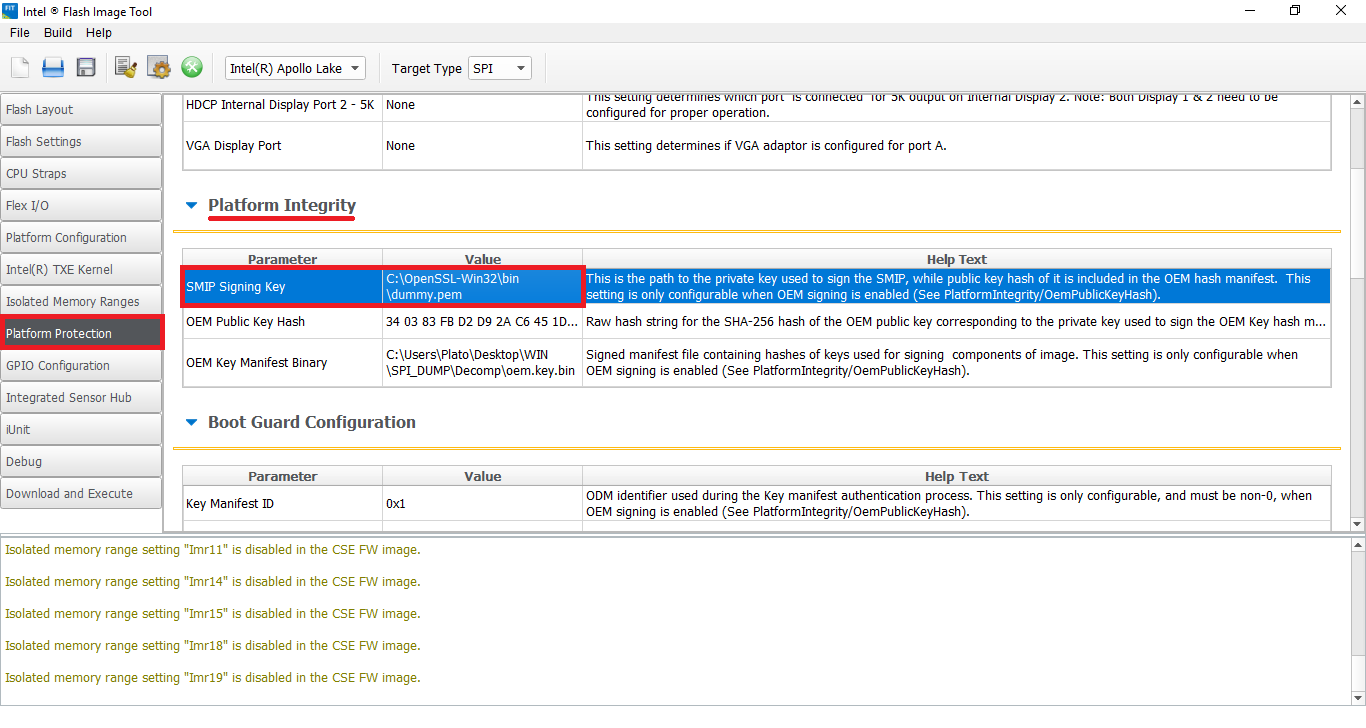
- At "SMIP Signing Key" field, input the placeholder RSA Private Key (dummy.pem) that was created by the OpenSSL tool. Then go to "Build > Build Settings", input the Manifest Extension Utility (MEU) executable location at "Intel(R) Manifest Extension Utility Path" field, input Win32 OpenSSL Lite 542 executable location at "Signing Tool Path" field, make sure that "OpenSSL" is selected at "Signing Tool" field, make sure that "Verify manifest signing keys against the OEM Key Manifest" is set to "No", leave all other settings intact and click Close.
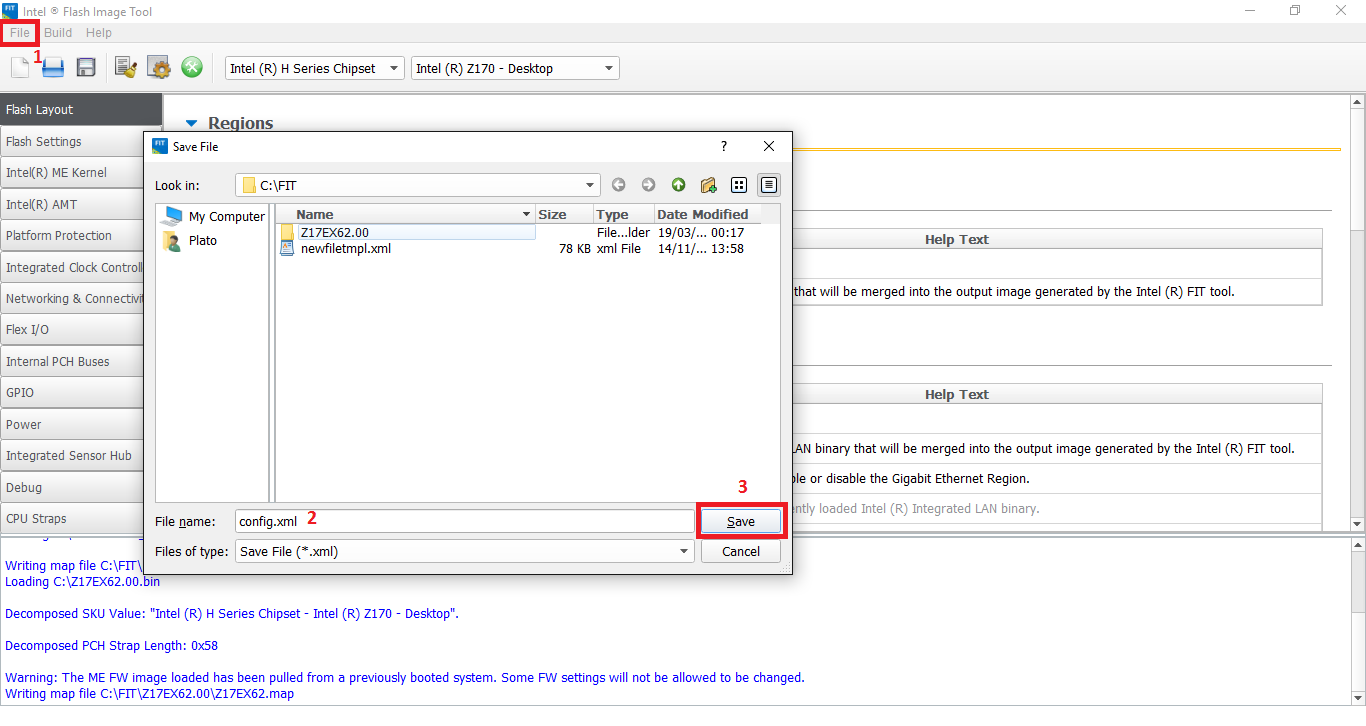
8. Go to "File > Save As" and save the configuration xml file, in this case it's named "config.xml". Afterwards, close the FIT window.
9. If you are working on a full SPI/BIOS image (Flash Descriptor + Engine + BIOS) and not a CSME 11 Engine region only (extracted via Flash Programming Tool with "-me" parameter or via UEFITool > ME region > Extract as is...), go to the FIT folder and there should now be a folder named after the inputted file, in this case it's named "Z17EX62.00". Enter "Decomp" subfolder. There should be a number of files there (BIOS Region, Flash Descriptor, OEM Region etc) including a "ME Region.bin" or "TXE Region.bin" or "ME Sub Partition.bin" or "TXE Sub Partition.bin" file. Take the previous "ME/TXE Region.bin" or "ME/TXE Sub Partition.bin" file you saved at step 4 and copy it where the current "ME/TXE Region.bin" or "ME/TXE Sub Partition.bin" file is, effectively replacing it.
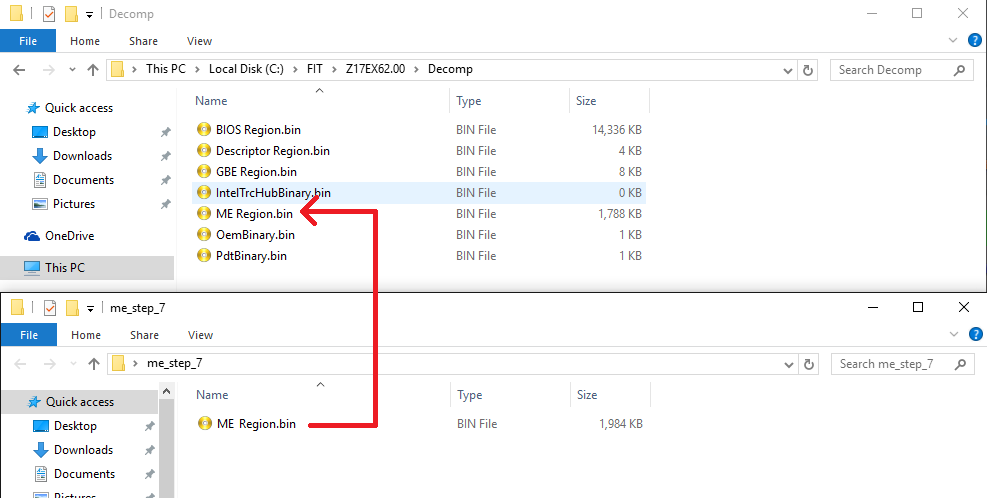
If you are working on a CSME 11 Engine region only (extracted via Flash Programming Tool with "-me" parameter or via UEFITool > ME region > Extract as is...) and not a full SPI/BIOS image (Flash Descriptor + Engine + BIOS), take the previous "ME/TXE Region.bin" or "ME/TXE Sub Partition.bin" file you saved at step 4, rename it exactly the same as the input file (Engine region) and copy it where the current input file is, effectively replacing it.
10. Run FIT again. From "File > Open" select the saved configuration xml file from step 8 and open it.
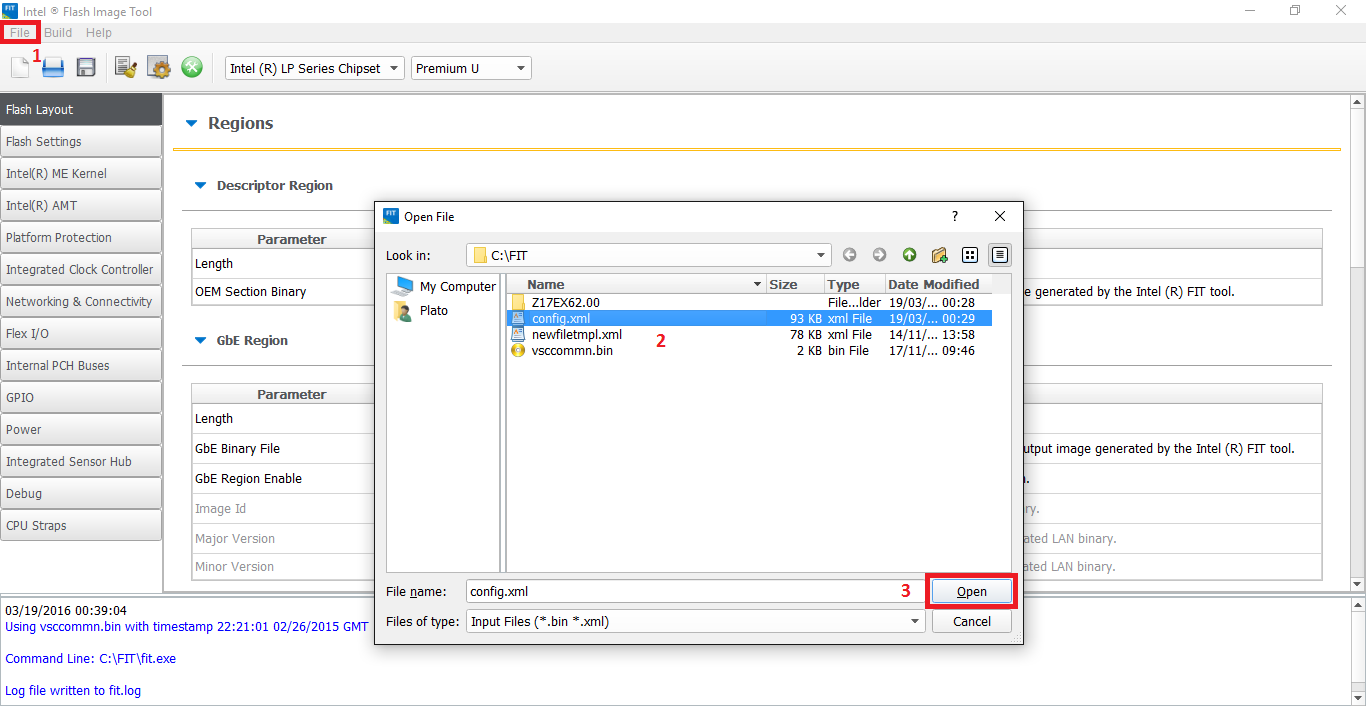
11. Click the "Build Image" icon (or "Build > Build Image") and it should complete successfully.
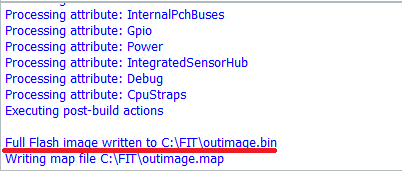
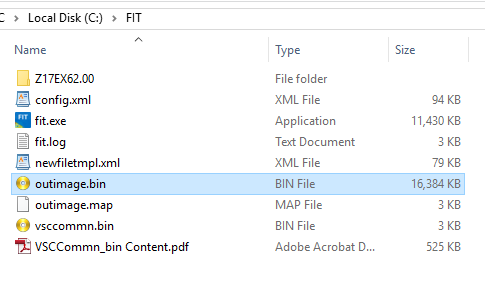
12. At the FIT folder you should now see a file named "outimage.bin" which is the dumped SPI/CSME/CSTXE image with an Engine region which has a Configured DATA section without any unneeded "Initialization" information stored.
13. If you are working on a CSTXE 3 - 4 SPI/BIOS image and you followed the instructions at Step 7 without skipping it, you determined that your SPI/BIOS image is signed by the OEM and thus inputted a placeholder RSA Private Key (dummy.pem) at "SMIP Signing Key" field. You must now restore the original OEM-signed SMIP module. For that you need to use a Hex Editor (example: HxD Hex Editor 45) and ME Analyzer 53 tool.
- Drag & drop the dumped SPI/BIOS image you want to clean at ME Analyzer and at Option(s) enter "-dfpt" parameter.
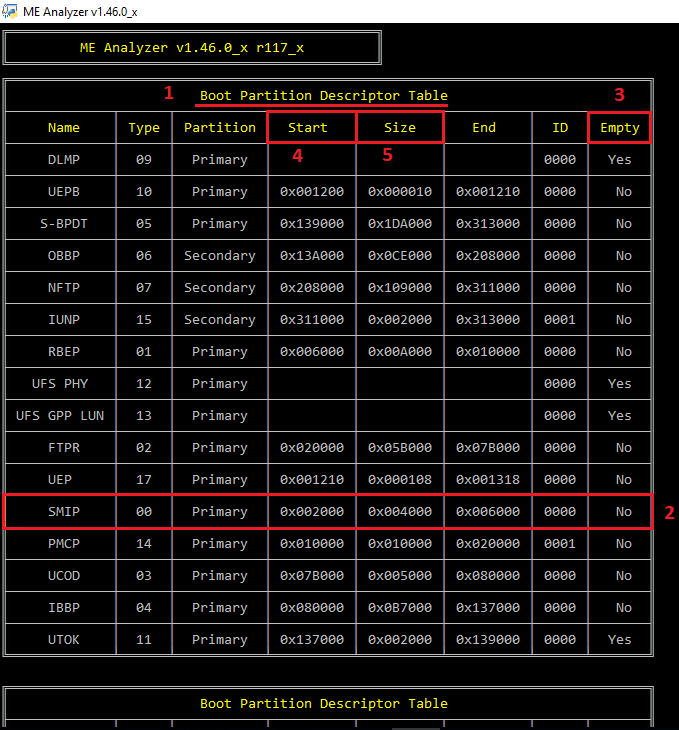
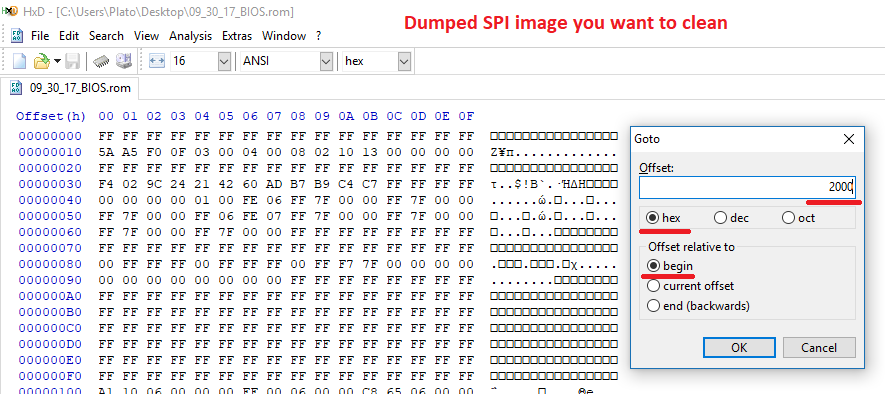
- Find the "Boot Partition Descriptor Table" which includes the entry with Name "SMIP". It must not be Empty ("No"). Note down SMIP partition's "Start" offset & "Size" which in this case are 0x2000 and 0x4000 respectively. Do the same for the "outimage.bin" file which got built at step 12. The SMIP "Start" offset & "Size" of both SPI/BIOS images are usually the same.
- Open the dumped SPI/BIOS image you want to clean as well as "outimage.bin" at the Hex Editor. From the the dumped SPI/BIOS image you want to clean, go to its SMIP "Start" offset and select a block equal to the SMIP "Size" which you noted down earlier. A block equal to the SMIP "Size" should now be selected. Do the same for "outimage.bin" file.
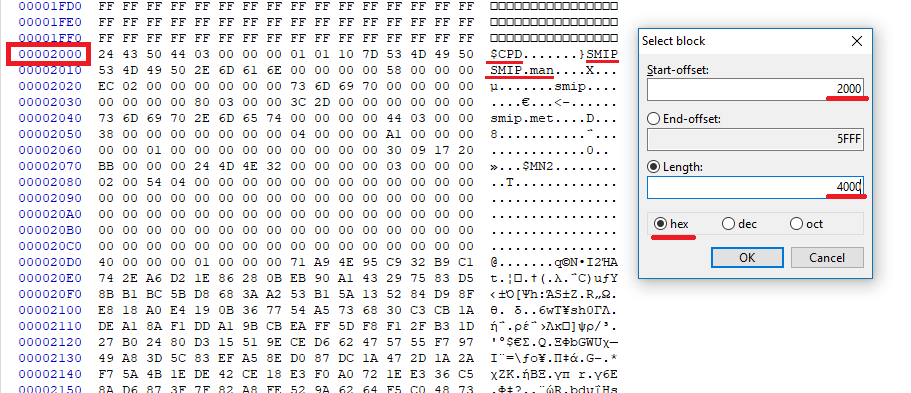
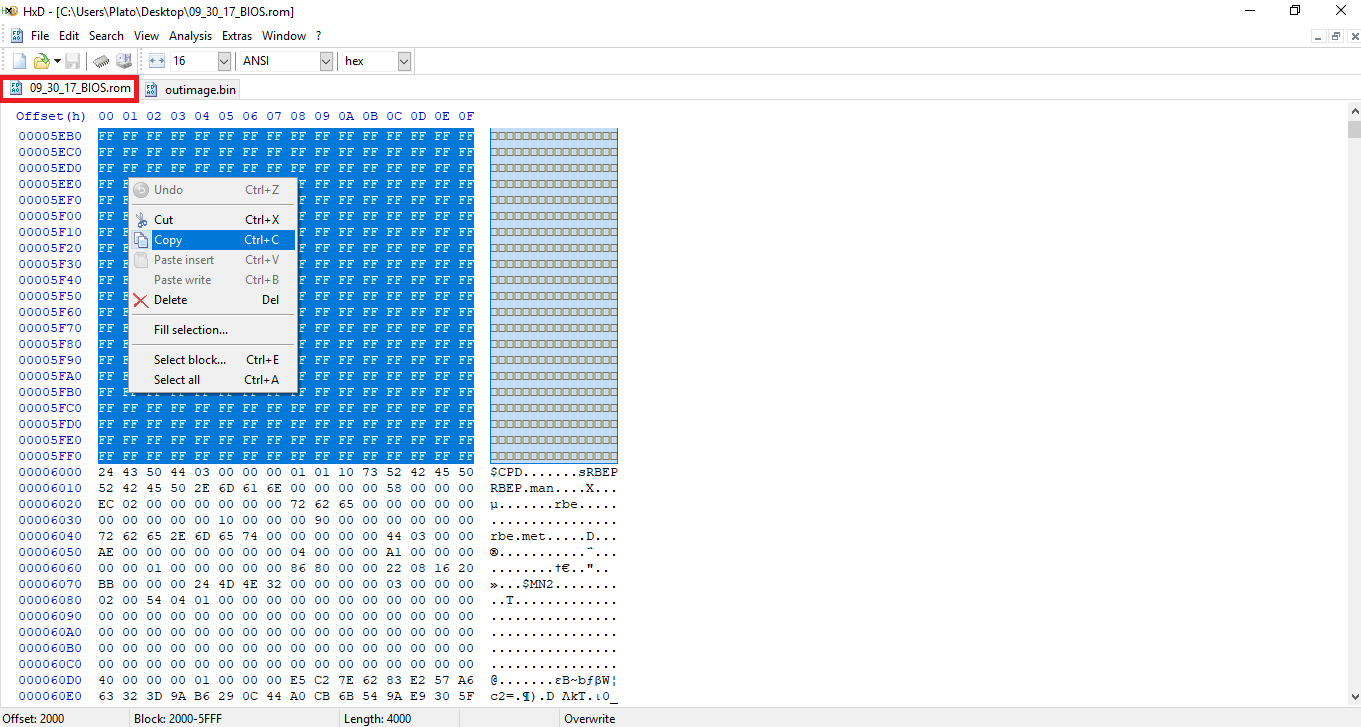
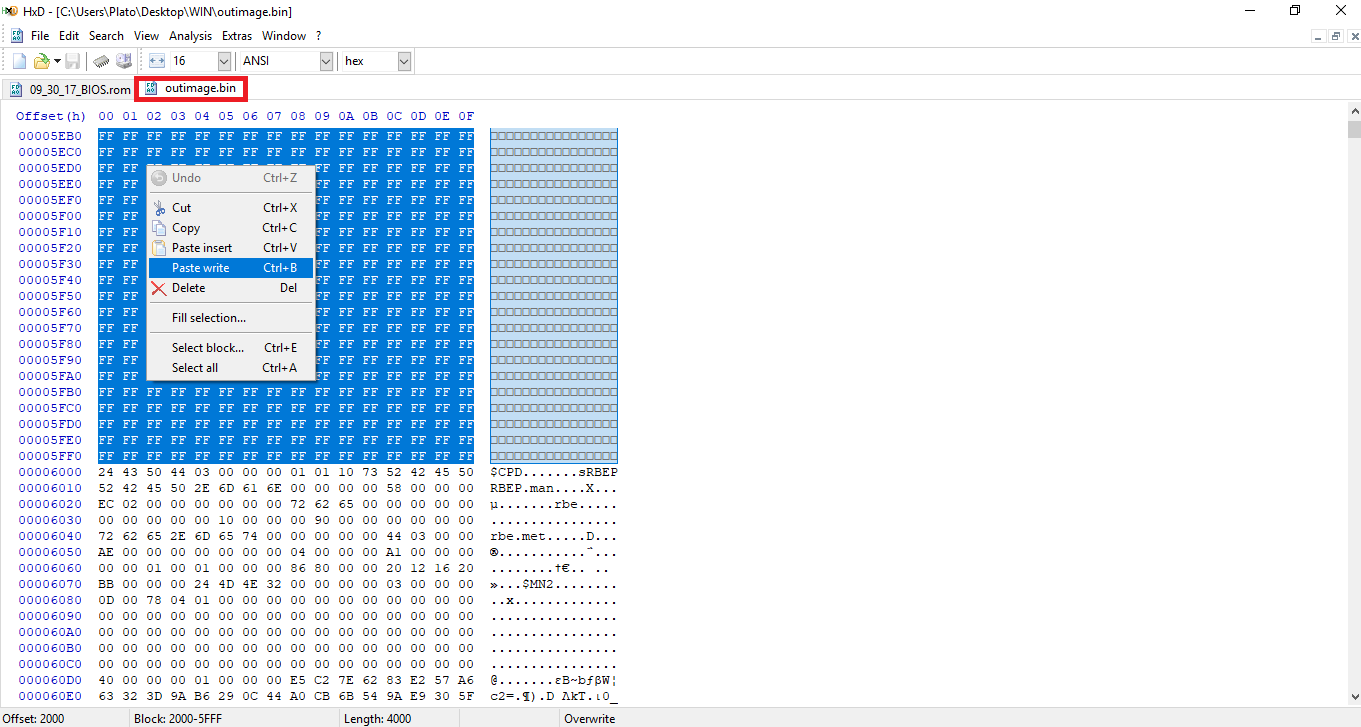
- Now you need to "Copy" the selected block from the dumped SPI/BIOS image you want to clean and "Paste write" it at the equivalent selected block of "outimage.bin". Then "Save" the changes at "outimage.bin" file.
14. Now, you need to verify that the resulting image ("outimage.bin") is indeed not Initialized. Import the output file to ME Analyzer and check if the Major/Minor versions, SKU & Stepping are the same as before. In order to verify that the DATA section is now Configured and not Initialized, make sure that the File System State is reported as "Configured".
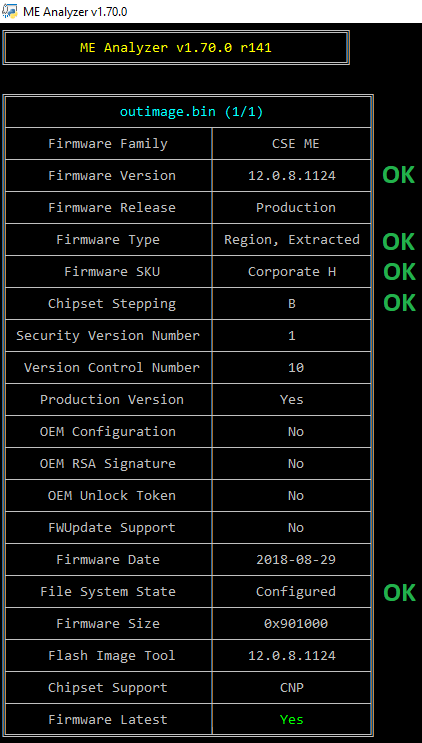
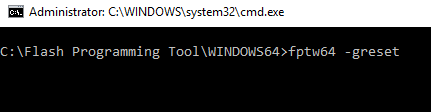
15. Last but not least, once your new cleaned+configured SPI/BIOS dump or Engine region is flashed on the target system, run Flash Programming Tool with command fpt -greset and wait for the system to reset (no settings are lost). This step is very important because it forces the Engine co-processor to re-initialize and properly accept any changes to its SPI/BIOS image region counterpart.
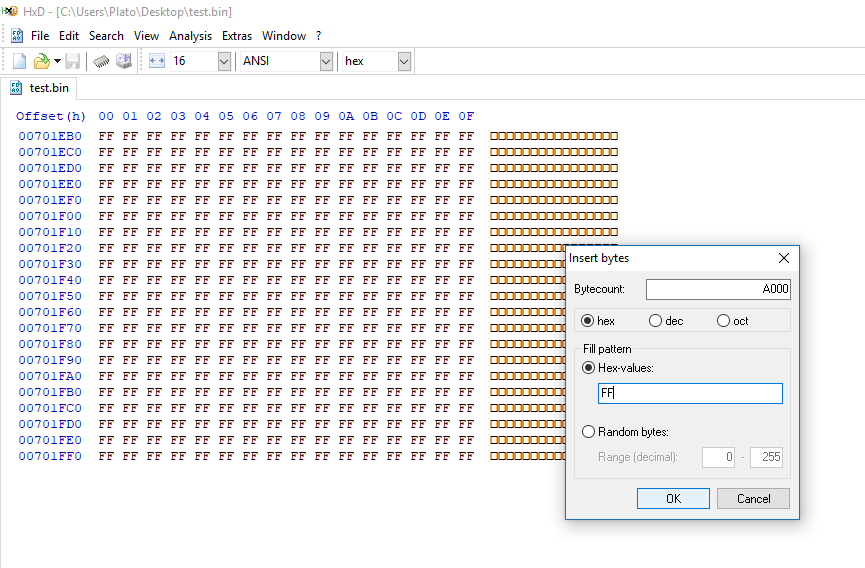
- If you are working on a CSME 11 Engine region only (extracted via Flash Programming Tool with "-me" parameter or via UEFITool > ME region > Extract as is...) and not a full SPI/BIOS image (Flash Descriptor + Engine + BIOS), make sure that the output region has the same size at the input/dumped one. To do that, subtract the output region size from the input/dumped one to get the difference, which is the amount of 0xFF padding that needs to be appended at the end of the output region using a hex editor. For example, in a hypothetical case in which the size difference is 0xA000, the output region would need to be adjusted in HxD Hex Editor 45 like so:
Download Flash image Tools:
👉 FITool-3.0.13.1144
👉 FITool-3.1.50.2222
👉 FITool-3.1.50.2240
👉 FITool-3.1.65.2309
👉 FITool-3.1.70.2340
👉 FITool-4.0.5.1280
👉 FITool-4.0.26.1337
👉 FITool-4.1.0.1031
👉 FITool-11.0.0.1166
👉 FITool-11.0.0.1173
👉 FITool-11.0.0.1180
👉 FITool-11.0.0.1191-r12
👉 FITool-11.0.0.1202
👉 FITool-11.0.0.1202-r17
👉 FITool-11.0.10.1002
👉 FITool-11.0.49.1536
👉 FITool-11.6.10.1196
👉 FITool-11.6.10.1196-r8
👉 FITool-11.6.20.1221
👉 FITool-11.7.0.1292
👉 FITool-11.8.50.3460
👉 FITool-11.8.55.3510
👉 FITool-11.8.65.3606
👉 FITool-11.8.77.3664
👉 FITool-11.8.79.3722
👉 FITool-11.8.86.3877
👉 FITool-12.0.0.1069
👉 FITool-12.0.2.1087
👉 FITool-12.0.2.1087-r7
👉 FITool-12.0.6.1120-r9
👉 FITool-12.0.20.1301
👉 FITool-12.0.22.1310
👉 FITool-12.0.40.1434-r20
👉 FITool-12.0.49.1536
👉 FITool-12.0.64.1551
👉 FITool-12.0.68.1606
👉 FITool-12.0.70.1652
👉 FITool-12.0.85.1919
👉 FITool-13.0.20.1312
👉 FITool-13.0.37.1556
👉 FITool-13.30.0.1065
👉 FITool-13.50.10.1252
👉 FITool-13.50.15.1475
👉 FITool-14.0.0.1061
👉 FITool-14.0.11.1205
👉 FITool-14.0.32.1122
👉 FITool-14.0.47.1500
👉 FITool-14.0.60.1790
👉 FITool-14.5.12.1112
👉 FITool-14.5.25.1229
👉 FITool-15.0.2.1337
👉 FITool-15.0.10.1447
👉 FITool-15.0.21.1549
👉 FITool-15.0.30.1716
👉 FITool-15.0.35.1951
👉 FITool-15.40.10.2268
👉 FITool-15.40.16.2534
<< Management Engine 7-10 & TXE 1-2

